Archive
PasteMiner – a pastebin monitor
Pasteminer is a monitoring tool for pastebin, with the following features:
- Multi-threaded (But it’s python, these two don’t mix very well)
- Proxy’s can be used to collect information
- Filters data using White List or Black List
- Filters can be a simple keyword, a Word List or a regular expression
TLDR -> pasteminer 🙂
Well this was something I coded a while back, I was doing some experiments with pastebin and used this to collect information about what was being uploaded.
I was doing this experiment for multiple reasons, but mainly to test a few theories. Well, first it’s a good way to keep up-to-date about the trending subjects that pull more users to open or view spam messages or to run virus. The usual and more common subjects are, iPhone jailbreak, movies, music, stollen and premium accounts etc. These guys don’t waste time they are up-to-date on what the users want!
As an example lately pastebin has been flooded with diablo3 “hacks/cracks” nothing more than scam/hacking attempts. So we can say that pastebin is a good source to get the latest malicious software samples about these subjects, to be dismantled and disabled stopping the operators before they manage to hit someone.
Continuing with diablo3 example, blizzard could gain some insight on how these pirates are working by simply keeping an eye on pastebin and other similar sources. Creating patterns and applying them in the “wild web” to detect these scam attempts on their products.
Pastebin is also used by hacking groups to post some of their achievements, usually this is done by posting private information about their targets. If a company is monitoring pastebin and some group posts sensitive information, an alert can be generated sent in matter of seconds, and in these subjects a quick response is everything.
This is the obvious and direct advantage of monitoring these sources, but this is just one among many. For example we can go further by “keeping an eye” at these leaked user data and checking if an employee of our company was a victim. This situation can be a huge security problem, because normally we use the same passwords for different services. When a situation like this is detected the compromised accounts can be disabled and a warning issued to the employee requesting to fix this problem.
While I was testing pasteminer there was an *individual* work submission of a class in my university, and just for fun I tried to see if anyone shared some code from the submission, to be clear I wasn’t attending that class :). Just in a few hours I was successful in this search since it was very easy to search for a couple of keywords.
There are a lot more of uses for a piece of software like this, these are just some of the most simple.
The code is very simple and may have/has some bugs, it’s not a piece of art but does it’s job as a POC very well. 🙂 served it’s purpose well. I wasn’t planing on realeasing it but changed my mind and decided to post this and I ended writing a lot more than I expected 🙂
Thank you for reading this even if it doesn’t have a single line of code!
ZeroCheck
Hello :),
I was testing an viewing the new crypto paste ZeroBin and two of it’s main disadvantages were the fact that a user has to trust the server for It’s anonymity and the Man-In-The-Middle on javascript.
Well tried to think of a way to protect the user and minimize these disadvantages. And came up with ZeroCheck.
What is ZeroCheck?
ZeroCheck is a chrome extension to fingerprint ZeroBin clones, it tries to make sure that a Zerobin clone is safe, this doesn’t mean that an approved website is safe because it can be keeping track of your IP address or some other connection info that may be used to track the person that made a paste.
SO A SITE MARKED AS SAFE BY ZeroCheck DOESN’T MEAN THAT YOU ARE 100% ANONYMOUS.
Only gives you some security about the version of the page and the libraries used on that website and the ability to check if the page or it’s libraries have changed in any way.
Where can I download ZeroCheck?
You can download it from the official github repository github.com/lbragues/ZeroCheck
What does it do?
This extension generates a unique fingerprint of the page and tries to detect any change on the core functions that may compromise the security provided by the zerobin original code.
It has two main features:
- Uniquely identifies the zerobin version of the javascript that is being used on the page.
- Uniquely identifies the page and checks to see if has been marked as a safe page.
Now a simple overview on how the extension works. If a website is detected as a zerobin clone a icon will show in the omnybox
The presence of this icon means that a website is a clone of the zerobin project, if you find any website that doesn’t show this icon and it’s a zerobin page then most certainly is because it’s in a iframe, so you need to open the real link of the page.
Example “http://www.anonpaste.tk/” the real url to the zeropaste is “http://www.peoplesliberationfront.net/anonpaste/index.php”
Notes:
Please keep in mind that this is a very simplistic approach to the problem, with this I mean that this extension may still have many bugs, and it certainly needs more work. 🙂
If you want me to check any website please leave a comment with his address here.
Tip: If you are getting some strange results use the refresh button 🙂
What kind of information can I get with ZeroCheck?
- Information about the crypto libraries used
- The classification of the website
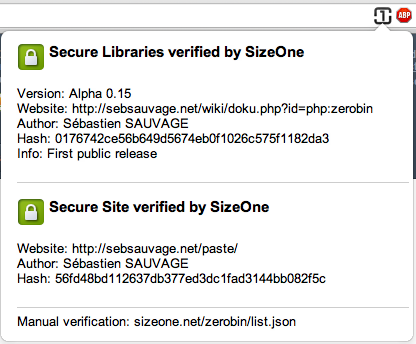
For example this is the info about the original ZeroBin site:
As you can see it show the information about the libraries used and their version and the website origin (This is manually checked to make sure it’s safe) If you open a website that wasn’t checked this is how it looks like:
This means that the libraries used are safe but the website hasn’t been manually checked.
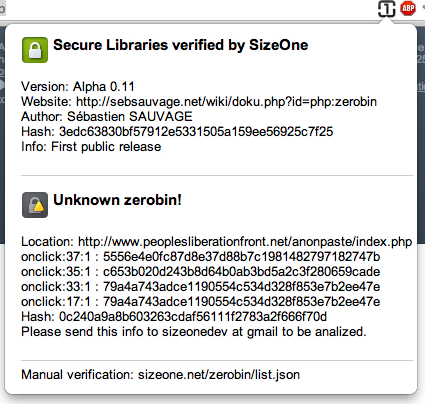
Now an example of unsafe libraries:
And for last an unsafe website:
shARPWatcher Protect your android phone from faceniff and droidsheep
shARPWatcher is an application to protect your android phone against arp spoof attacks, used by software like faceniff and droidsheep. 
This application has two modes:
- Rooted phone – Preemptive mode: As soon has your device connects to a network it prevents all spoof attacks, rendering them useless (Low battery consumption and 100% bullet proof).
- UnRooted phone – Best Effort mode: It keeps monitoring your phone, from time to time, searching for attacks if it detects one and the disconnect on attack option is on it deactivates your wifi, otherwise sends an alert.
To be completely protected against these attacks you need to have a rooted phone, otherwise there’s always the chance the attacker gets what he wants.
[How to install]
Simply go to android market and search for “sharpwatcher”, follow this market link or read the qrcode. 🙂
[How to use]
It’s very simple to use and you almost don’t need to configure anything.
- Tap the shield image to turn on or off (Green WiFi symbol On, Red WiFi symbol off)
- You need to turn on or off with your WiFi disabled, turning on with an already connected WiFi may not protect you.
Rooted phone (Preemptive mode) it’s all you need to know… 🙂
For UnRooted devices (Best Effort) you still have one more option!
- Disconnect under attack check box
If you have this option checked when an attack is detected shARPWatcher will disable your WiFi preventing any further damage. If this option if off then it will send a notification warning you that it detected an attack.
IMPORTANT: If sometimes on preemptive mode your connection seems to stop working for a while it’s not shARPWatcher fault. It means that you are under attack and it’s not working for the attacker 🙂
sslstrip mod to support plugins
This program is distributed in the hope that it will be useful, but
WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
This is my modification of sslstrip to support plugins.
setup.py was removed so you cant install directly this version
use it only from the folder
I created this to help me on some tests I did, it got a lot easier. This code isn’t perfect, far from it…
For someone that hasn’t much experience in python this was made in record time… don’t be too hard on the errors
it might have.
Screen shots:
Installing:
- Do it like you where installing normaly sslstrip
- Don’t use setup.py wont work. This is a experimental version.
Running:
-
To activate plugins add the -x or --s1plugin option in the command line
####### Plugin Info #########
File structure:
s1plugin
|____ plugins (All plugins are here)
| |____ _OSFinder (Plugin folders, each plugin has it’s own folder)
|____ * (All the other files, you don’t need to change anything)
It’s easy, so if you know what you are doing you shouldn’t have a problem understanding
if you can’t then don’t change anything 🙂
About plugins folder:
- A plugin is only loaded if it’s folder HAS the file __init__.py
- Deactivating a plugin Rename or remove “__init__.py”
- To be loaded a Plugin must have a file named S1Plugin.py with a class named S1Plugin respecting the rules
Plugin class:
- EventSender it’s an empty plugin, you want to create a new one use that and remove what you don’t need
- What can you do and listen: (I think I don’t need to explain)
- onResolveHost(self,client,host,result)
- onHostResolvedSuccess(self,client,address)
- onHostResolvedError(self,client,error)
- onCleanHeaders(self,client,headers,result)
- onClientConnection(self,host,headers,client,path,postData,url)
- onSendSpoofedFaviconResponse(self,client,icon_path)
- onProxy(self,client,host, method, path, postData, headers, port, ssl)
- hijackConnection(self,client,url,clientConnection)
- onVisitUrl(self,client,url,postData)
- injectContent(self,client,contentType,data)
- Store and read values on disk (settings.db) -> sqlite3
- storeValue(“key1″,”ohhyeah”)
- readValue(“key1”)
- Communicate between plugins
- View _OSFinder and UrlLogger plugins for reference
Modifications on sslstrip.py:
Find this:
print “\nsslstrip ” + gVersion + ” by Moxie Marlinspike running…”
Here:
# —— SizeOne Mod —————————————
# import The event manager class if detected
if(os.path.exists(“s1plugin”)):
from s1plugin.S1StrippingProxy import S1StrippingProxy
#create replace normal classes
strippingFactory.protocol = S1StrippingProxy
# ———————————————————-
I think it’s all I have to say for now
More Info:
https://github.com/lbragues/sslstrip
Heroes of Newerth Resource Editor
Hi, before anything else, this is a tool to edit the s2z files of the HoN (Heroes of Newerth) game.
This tool isn’t any thing “new” since these files format is public, it’s aim is to make their edition easier to every one with a few clicks. Don’t be expecting something completely overwhelming it’s in the early stage and it has a lot of bugs. It’s evolution depends directly on the acceptance it will have on the community and the number of people using it. It’s completely free, there aren’t any drawbacks or pro versions.
Keep in mind that this tool isn’t made by any company and it’s made exclusively on the spare time of a single person. So if you wish to contribute with anything use the Paypal buttons. 🙂
IMPORTANT: I will not take any responsibility for any harm done by this tool. USE AT YOUR OWN RISK!
So I think now is the time to start explaining how this works…
Requirements:
- Java Virtual machine installed and on the latest version.
Operating Systems:
- Windows 7 (Working)
- MacOSX Snow Leopard (Working)
- Linux (Not tested should be working)
- It Should work on any System that has JavaVM installed.
(If you test it on any other platform send some feedback and I’ll update these infos)
So if you download the tool you should have the following files and folders.
- default.png – Default icon used when you create a *.honmod
- SizeOneHoNRELauncher.jar – This is the one you should run it will check for updates
- SizeOneHoNResources.jar – The application, if you run this it will start the launcher
- extract – (Folder) It’s where all the files you extract will go to.
- lib – (Folder) This folder contains all the necessary libs to run the application (Don’t mess with this folder)
- mods – (Folder) This is the default folder where the program stores your mods.
- tmp – (Folder) Folder to store temporary files (You may delete it’s contents if you want)
If your application crashes it will send me a report with your operating system application version and the actual error.
You shouldn’t be able to run the SizeOneHoNResources.jar directly.
Features:
- Viewing and Extracting contents of an *.s2z, *.honmod file (Any zip file :))
- Creating New mod files (resourcesXXX.s2z or *.honmod)
- Editing this files (add, remove, replace)
(Expect a few more features in the near future)
Tutorial:
Downloads:
Special Thanks to bezta that made the icons and graphics 🙂
Any suggestions just send me an email 🙂